
Flipper Zero has been on my desk for a while now, and it’s the kind of tool that sneaks up on you. At first glance, it appears to be a Tamagotchi for hackers; a cute dolphin on a tiny screen. However, beneath the surface, it can ping RFID cards, mimic remotes, interact with NFC, and detect signals that most people never notice.
That mix of playful and powerful is what makes it addictive. Still, I began to encounter its limitations. It’s versatile, yes, but it doesn’t dig as deep as some specialized gear and with stock shortages and import bans emerging in various countries, relying on just one device doesn’t seem smart.
So I went hunting. I tested five other tools that security folks swear by. Each one brings something Flipper can’t, which is more range, more focus, or more brute force. Here’s what I found.
Flipper Zero: What it is and why i am looking for alternatives

The Flipper Zero markets itself as a portable multi-tool for hackers and security enthusiasts. After spending time with it, I’d say that description holds up. It’s about the size of a chunky remote, with a tiny monochrome screen and a toy-like dolphin mascot that reacts to how much you use it. It feels playful, but the hardware inside is no joke.
In my testing, the Flipper handled a wide range of protocols:
- RFID (125 kHz) – reading and emulating low-frequency access cards.
- NFC – interacting with tags, payment cards, and smart devices.
- Sub-1 GHz radio – capturing and replaying signals like garage doors or key fobs.
- Infrared – working as a universal remote.
- iButton – those old-school digital keys.
- Bluetooth LE and GPIO pins – for more advanced tinkering or pairing with external modules.
What struck me is how accessible it makes all this. Most devices that handle even one of these protocols require additional setup, a laptop, or a considerable amount of technical expertise. The Flipper wraps them together in a pocket-sized shell that doesn’t need a PC to run. Just scroll the menu, choose what you want, and it works. That simplicity is why it became a cult favorite, especially among beginners.
But there’s another side. The more I pushed it, the more I felt its limits:
- Sub-GHz radio – good for replay attacks, but not powerful or flexible enough for deeper SDR work.
- NFC support – decent for casual use, but nowhere near the depth of a specialized tool like the Proxmark3.
- User interface – simple for quick tasks, yet cramped once you move past basic testing.
- Availability issues – in some regions, shipments get blocked at customs, and Amazon has even banned sales. Resale prices can spike, making it more challenging to obtain one at a fair price.
Flipper Zero is a great entry point, but it’s not the end of the road. If you want to delve deeper into RF, NFC, or Bluetooth, specialized tools are available. That’s where my search for alternatives began.
Next, let’s see the tools that came out ton op from my various tests.
1. HackRF One

HackRF One felt very different from the Flipper Zero the moment I tried it. Where the Flipper looks like a toy, HackRF One is all business. It’s a bare circuit board with ports and antennas sticking out. It doesn’t charm you with a mascot, and it doesn’t run on its own in your pocket. What it gives instead is raw radio power.
Features and capabilities
The HackRF One is a software-defined radio (SDR) that spans a massive frequency range, from 1 MHz to 6 GHz. That means it can listen to and transmit across almost anything wireless: FM radio, Wi-Fi, Bluetooth, GSM, satellites, garage doors, even weather balloons if you feel like chasing one. Paired with software like GNU Radio or SDR#, the flexibility is enormous.
During my tests, I used it to:
- Capture and replay basic RF signals.
- Visualize spectrum activity across wide ranges.
- Experiment with GSM and Bluetooth packets.
- Dive into SDR tutorials that Flipper Zero could never handle.
The learning curve is steeper because HackRF isn’t a plug-and-play gadget. You need a laptop, the right software, and patience to configure everything. But once it’s running, it gives you a sandbox that makes Flipper’s sub-GHz functions look like child’s play.
HackRF One Pricing
The HackRF One is a versatile Software Defined Radio (SDR) that offers a wide frequency range from 1 MHz to 6 GHz. Its pricing varies based on the bundle and accessories included. On Nooelec, the base unit is priced at $319.95, while a complete bundle with an ANT500 antenna and SMA adapters is available for $349.95. Other retailers, such as SparkFun, offer it for $339.95. For those seeking enhanced performance, Nooelec provides a version with a 0.5 PPM TCXO installed in a black aluminum enclosure for $389.95 .
What I liked
The range and depth are unmatched. With the right antenna, I was able to monitor signals from devices well beyond Flipper’s limited reach. The open-source ecosystem around HackRF is also strong—you’ll never run out of projects or tutorials. For anyone serious about wireless security research, this tool feels like stepping into a much larger playground.
What I didn’t like
It’s not portable in the same way. You can’t whip it out to quickly emulate an NFC badge or turn off a TV; it always needs a computer tether. The setup process can be frustrating if you’re new to SDR, and there’s a real risk of accidentally transmitting in frequencies you shouldn’t. Unlike Flipper, which guides you into safe experimentation, HackRF is only as careful as you are.
Verdict
HackRF One isn’t a Flipper replacement—it’s a step beyond. If you want to dive deep into radio and don’t mind the complexity, it’s one of the most capable alternatives out there. For me, it turned wireless hacking from a hobby into a study.
2. Proxmark3

When I first picked up the Proxmark3, it felt less like a gadget you play with and more like a lab instrument. It doesn’t try to be flashy or beginner-friendly; it’s a serious tool made for people who want full control over RFID and NFC. Compared to the Flipper Zero’s friendly interface, the Proxmark3 almost dares you to know what you’re doing before you touch it.
Features and capabilities
The Proxmark3 is a powerhouse for working with RFID systems. It supports both low-frequency (125 kHz) and high-frequency (13.56 MHz) cards, and it can:
- Read and write the most common RFID and NFC tags.
- Emulate cards so you can mimic access badges or fobs.
- Sniff and intercept communication between a card and a reader.
- Perform cryptographic attacks on certain protected systems.
- Run custom scripts for advanced testing.
In my testing, it handled cloning simple RFID badges effortlessly, but it really stood out when analyzing secure NFC protocols. This is where Flipper Zero usually taps out—Proxmark3 lets you capture raw data, inject commands, and break down authentication step by step.
Proxmark3 Pricing
The Proxmark3 is a specialized tool for RFID and NFC research. Its pricing varies depending on the model and vendor. The Proxmark3 Easy 3.0 is available on Amazon for approximately $90. For more advanced features, the RDV4 kit is priced at $150 on Hacker Warehouse. Additionally, the PM3 Proxmark3 Master Ultimate Version with an OLED display and battery is available on eBay for around $120.
What I liked
The depth is unmatched. If you’re serious about RFID security research, this is the tool that opens doors Flipper can’t. I loved how precise it felt—you’re not just pushing buttons, you’re running commands that give you full visibility into what’s happening between tag and reader. There’s also a huge community backing it, with tutorials, firmware updates, and attack scripts constantly circulating.
What I didn’t like
It’s not portable or beginner-friendly. Unlike Flipper Zero, you can’t just scroll a menu and clone a card in seconds. You’ll need a computer, drivers, and time to learn the command-line interface. The hardware itself is also bulkier, and if you’re just looking for quick tricks, it’ll feel like overkill.
Verdict
The Proxmark3 isn’t trying to be fun—it’s trying to be complete. For casual experiments, Flipper Zero is still the friendlier option. But if your focus is RFID and NFC, and you don’t mind the steeper learning curve, Proxmark3 is one of the strongest alternatives out there. It taught me more about card systems in a week than months of tinkering with the Flipper ever could.
3. Ubertooth One
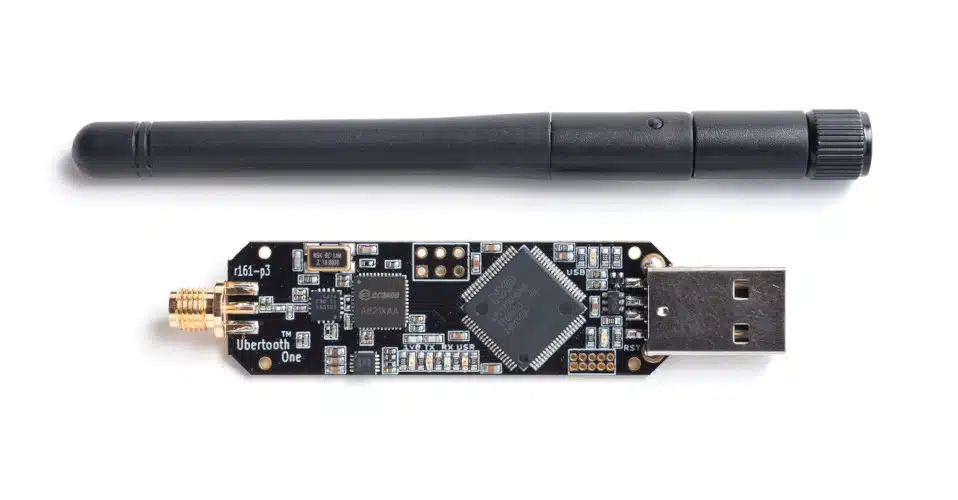
Ubertooth One doesn’t look like much at first—it’s a small USB board with an antenna, not nearly as polished as the Flipper Zero. But once I plugged it in and started capturing Bluetooth signals, I realized how specialized this tool really is. If HackRF is a wide net for radio, Ubertooth is a scalpel aimed directly at Bluetooth.
Features and capabilities
The Ubertooth One is an open-source Bluetooth development and security tool, with a particular focus on Bluetooth Low Energy (BLE). Unlike general-purpose radios, it’s designed to sniff, monitor, and analyze Bluetooth traffic in real time.
With it, I was able to:
- Capture BLE packets as they flew between devices.
- Identify nearby devices broadcasting over Bluetooth.
- Run active tests on pairing processes.
- Visualize traffic patterns with Wireshark integration.
This makes Ubertooth invaluable for anyone testing wireless peripherals, IoT devices, or even Bluetooth-based locks and trackers. It doesn’t just tell you what’s nearby—it lets you peek under the hood.
Ubertooth one pricing
The Ubertooth One is an open-source Bluetooth development and security tool. Its pricing is relatively consistent across various retailers. On Hak5, it is priced at $120. Similarly, PiShop offers it for $120. For those looking for a more budget-friendly option, eBay lists it for as low as $55.12 when purchasing multiple units.
What I liked
The focus is razor sharp. Instead of juggling multiple protocols, Ubertooth focuses deeply on Bluetooth, and it does that one thing extremely well. I liked how quickly I could fire it up with Wireshark and start capturing live traffic. The open-source community is also strong, offering scripts, tools, and guides for real-world Bluetooth experiments.
What I didn’t like
Range is limited without upgrading the antenna, and setup can be a little finicky depending on your OS. It’s also not as versatile as other alternatives—you won’t be cloning RFID cards or playing with sub-GHz remotes here. If you’re after a multi-tool, this won’t cut it. But if Bluetooth is your playground, it’s perfect.
Verdict
Ubertooth One feels less like an all-in-one gadget and more like a specialist’s kit. For Bluetooth research, it’s hard to beat. It gave me visibility into a wireless protocol that Flipper Zero only scratches the surface of. If your work or curiosity revolves around Bluetooth devices, Ubertooth is the natural next step.
4. Yard stick one

When I first unboxed the Yard Stick One, I was struck by how simple it looked like just a small USB dongle with an antenna sticking out. No mascots, no flashy casing, just a tool that gets straight to work. But as soon as I started testing it, I realized this little device packs a serious punch in the sub-1 GHz radio world.
Features and capabilities
Yard Stick One is a USB transceiver explicitly designed for sub-1 GHz frequencies. That’s the band used by key fobs, garage doors, remote sensors, and many IoT devices. Unlike the Flipper Zero, which can replay simple signals, Yard Stick One gives you full control over modulation, encoding, and packet timing. During my testing, I could:
- Capture and decode sub-1 GHz signals from wireless remotes.
- Replay and fuzz signals to test device responses.
- Work with popular protocols like OOK, FSK, and ASK.
- Integrate with software like GNU Radio or Universal Radio Hacker for advanced analysis.
This made it perfect for anyone wanting to dig deeper into RF security. Flipper Zero is convenient for quick experiments, but Yard Stick One lets you see the raw data, tweak it, and test the limits of a device’s radio security.
Yard stick one pricing
The Yard Stick One is a sub-1 GHz wireless transceiver designed for RF experimentation. Its pricing varies slightly based on the retailer. On Nooelec, the base unit is priced at $151.90, while a bundle with an ANT500 antenna is available for $170.75. Adafruit offers it for $99.95. Hacker Warehouse lists it starting from $110, with optional accessories available for an additional cost.
What I Liked
The precision and control are unmatched. I could capture a signal from a wireless door sensor, decode its packets, and even modify them to see how the system reacted—all things Flipper Zero can’t do on its own. It’s also very lightweight and portable, so you can easily take it to field tests. The strong software support and open-source tools made experimenting intuitive once I got past the initial setup.
What I didn’t like
This isn’t a beginner-friendly tool. You need some familiarity with SDR concepts, RF protocols, and software like Wireshark or GNU Radio to make the most of it. Out of the box, it won’t emulate NFC or read RFID cards—it’s laser-focused on sub-1 GHz, so versatility takes a backseat. If you’re looking for a multi-tool like Flipper Zero, this one feels specialized for pros.
Verdict
Yard Stick One is for anyone serious about RF security in the sub-1 GHz band. It gave me insights into wireless protocols that Flipper Zero only brushes over. If your experiments revolve around garage remotes, wireless sensors, or custom RF devices, this is a must-have in your kit.
5. M1 Multitool

The M1 Multitool caught my attention because it promised versatility, kind of like a Flipper Zero but with a more pro edge. When I held it, it felt solid, more substantial than the Flipper, and the interface looked approachable. Unlike Yard Stick One or Ubertooth, which focus on a single protocol, M1 aims to be a jack-of-all-trades with an emphasis on RFID, NFC, and smart card systems.
Features and capabilities
The M1 Multitool is designed for security researchers and penetration testers who want portability without giving up depth. In my hands, it could:
- Read, write, and emulate a variety of RFID tags, including MIFARE Classic, DESFire, and NTAG.
- Interact with NFC-enabled cards and devices with advanced security.
- Run quick scripts or preloaded commands for card testing.
- Log and export data to a PC for further analysis.
I was able to clone a MIFARE Classic badge in seconds, a task that Flipper Zero can also handle, but M1 provided me with more control over sectors and keys. It also handled some high-security NFC systems that Flipper struggled with, making it a versatile portable tool for field work.
M1 multitool pricing
The M1 Multitool is a compact device designed for RFID and NFC research. Its pricing varies depending on the vendor and any ongoing promotions. Vice Hardware offers it for $99.99, discounted from the original price of $155 . Discount Cutlery lists it for $113.10. TechVolt offers it for $119.
What I Liked
It strikes a nice balance between portability and power. I could carry it around like Flipper Zero, yet dive deeper into card protocols without needing a full lab setup. The interface is clean, the menus are easy to navigate, and it comes with helpful software for Windows, macOS, and Linux. I appreciated having a tool that lets me switch from quick tests to more advanced attacks seamlessly.
What I didn’t like
It’s not perfect. While versatile, it doesn’t cover RF beyond RFID/NFC, so it won’t replace HackRF or Yard Stick One for broader wireless work. Battery life can be limiting if you’re out in the field for hours, and advanced functions sometimes require connecting to a PC. Compared to Flipper Zero, it’s slightly less fun to use because it’s clearly made for serious testing.
Verdict
The M1 Multitool is a portable powerhouse for RFID and NFC research. For me, it became the go-to when I needed depth without dragging out a laptop and a Proxmark3. It won’t replace every specialist tool, but it’s a perfect blend of accessibility and capability for those serious about smart card security.
Wrap up
Testing these Flipper Zero alternatives showed me just how much depth there is beyond an all-in-one device. Flipper Zero is excellent for getting started. It’s portable, playful, and covers a wide range of protocols, but once you want to specialize, other tools take over.
HackRF One gave me access to the full radio spectrum, opening possibilities for experiments I couldn’t do on Flipper. Proxmark3 revealed the intricate workings of RFID and NFC, making card cloning and analysis much more precise. Ubertooth One focused on Bluetooth, allowing me to monitor and analyze devices in real-time. Yard Stick One provided control over sub-1 GHz devices, ideal for remotes and sensors, while M1 Multitool combined portability with depth for smart card work in the field.
Ultimately, these tools aren’t about replacing Flipper Zero, but they can help expand your toolkit. Depending on your focus, any one of them can take your security research and experimentation to the next level.











